Hybrid and remote work, mobile devices, and public clouds are a permanent fixture in the corporate world. While efficient and convenient, they also pose greater challenges. It is no longer enough for data admins to configure their organisation’s network and put it behind a firewall. Security is a two-way street and users need to pull their weight as well. Let’s take a closer look at Google Workspace security, best practices for users and advanced features for admins to ensure your sensitive business data is safe.
The concept of maintaining security in the public cloud is based on the Shared Responsibility Model. In this framework, the cloud provider is responsible for the security of the infrastructure it creates, while the user independently secures access to their data, systems, and applications. First, let’s look at how Google protects the security and privacy of its users and then what you need to do on your end.
Since hiding corporate data and resources behind a wall proves to be a fragile system, many software providers, including Google Cloud solutions, have embraced the Zero Trust security model. It involves constant “vigilance” in user verification and endpoint management and flags any suspicious activity. Rather than checking user credentials “at the gate,” i.e. when logging into the company network, Zero Trust policies verify each user request to access each asset. This way Google protects your sensitive content from both external bad actors and from insider threats.
Company data security
It takes two to tango, however, even when using the most secure software. In fact, up to 99% of security incidents occur due to user negligence. For this reason, Google admin console provides a range of tools to help admins protecting user accounts from data leaks. These include password strength control, enforcing two-factor authentication, and using a security key (U2F). If your organisation stores data in the cloud, as is the case of most companies these days, it is accessible from all devices where users are logged in. Find out what your employees need to be aware of and what your admins can do to make your data safer.
5 best practices for Google Workspace users
1. Regularly Check Passwords
Google has developed recommendations for creating strong passwords to help users safeguard their accounts. When creating a character string that guards your data, follow these guidelines:
- Create a password with a minimum of 12 characters (though security experts say 14 or 15 characters is better).
- Include UPPERCASE letters, lowercase letters, numb3rs, and $ymbols in the password.
- Avoid passwords that can be guessed by people who know you personally (e.g., pet names).
- Don’t use passwords containing public information about you (e.g., birthdays).
- Avoid common words and key combinations like “qwerty” or “password1234.” (you would be surprised how many people still use those).
- Always create unique passwords for important accounts and don’t reuse them (especially if your former password was stolen).
Your Google account has a built-in security audit tool in the form of a password manager. You can use it to check if the passwords saved on your accounts are weak, reused, or potentially compromised by someone else. How to use this tool:
- On your computer, go to passwords.google.com.
- Select “Check passwords” and log in to confirm your identity.
- Review the list of password recommendations, and if necessary, improve any that are unsafe to better protect your accounts.
2. Enable Two-Factor Authentication (2FA)
Two-factor authentication (2FA) is an additional layer of security that prevents malicious actors from accessing your account, even if they obtain your password. In 2FA, a physical device you always have with you, usually a phone or a special security key, is involved in the login process.
Google’s 2FA can be configured in various ways, ensuring the account owner has several secure methods to confirm their identity. The available features include:
- One-time texts sent to your phone.
- Verification codes delivered through a phone call.
- Google Authenticator app for generating codes even without an internet connection.
- Backup phone number for receiving codes if something happens to your smartphone.
- Printable backup codes for future use.
- Registering trusted devices to skip the second step during login.
Using a security key instead of a code
A U2F security key is safer than phone-based verification because it eliminates the risk of code interception by malicious software. It is also small, similar to a USB drive, and universal – one key can authorise logins to multiple accounts, including those outside the Google ecosystem.
It’s a good practice to set up more than one verification method, such as using both a USB key and a phone. You can configure additional verification steps in the “Security” > “Two-factor authentication” section.
3. Monitor logged-in devices
Failing to log out of your account on devices that others can access is a mistake that can happen to anyone. Fortunately, in the “Security” section on the website https://myaccount.google.com/, you can always check which devices are currently logged into your account.
Click on “Manage devices” and carefully review the list of devices connected to your account. For security reasons, log out of any devices you don’t use regularly. Each computer, smartphone, and tablet will also provide information about the last activity date, first login, and approximate location.
If you see a device you don’t recognise on the list, report it to Google to initiate the account protection process.
4. Lock Device Screens
Like most people, you probably don’t log out of your Google account on your personal devices every day because you plan to have them with you at all times, and you’re the only user. If your phone, tablet, and laptop don’t have strong screen locks, they can be a potential security gap for your Google account.
Set screen locks on these devices that activate after no more than e.g. three minutes of inactivity, and require a unique PIN, password, or biometric verification (fingerprint, facial scan, or iris scan) to unlock. This way, even if you lose your portable access point to your Google account, you’ll make it significantly more difficult for unauthorised individuals to access the data stored on it.
5. Consider joining the Advanced Protection Program
If you’re a journalist, activist, or belong to a group of individuals at risk of online attacks, consider enrolling in the Advanced Protection Program to access enhanced security features.
Using Advanced Protection requires the use of a security key and completing account recovery information. How will your daily use of Google apps change?
- Many untrusted apps will be blocked.
- You’ll receive more frequent alerts and notifications before downloading files or installing apps. (Advanced Protection conducts even more rigorous scans for potential threats than basic Google services.)
- Security features on your account, which are optional for most users, will be automatically enabled.
4 Google Workspace security tools for admins
Even with all the user safeguards in place, companies that handle sensitive information may wish to amp up their security even more. The three most important security management tools available in the Google Workspace (Enterprise package) include: the Security Center, Data Loss Prevention rules for Drive, and Context-aware access. Another highly useful application is Google Vault.
1. Context-aware access
Context-aware access is a tool that allows you to specify detailed guidelines for both access to the entire Google Workspace account and selected applications in the package. These rules can be based on attributes such as device security status, user identity, location, or IP address.

With context-aware access, the administrator can allow access to the Google Workspace account only on company computers, devices protected by strong passwords, or only within the corporate network. This solves the problem of unauthorised login on a personal device, threats of sensitive data leaks. By using context-aware access correctly, you can ensure that the device is protected by a PIN, and the company’s internal data remains secure.
2. DLP rules for Drive
Google Workspace allows users to create Data Loss Prevention (DLP) rules for Google Drive. These rules help better protect sensitive corporate information from external data sharing. In practice, this process works as follows:
The administrator creates a DLP rule in the instance, specifying what content needs protection (e.g., credit card numbers, contracts, personal data), which events are considered unwanted (e.g., sharing a file with someone outside the organisation or working in a different department), and how the system should respond when an incident is detected (e.g., block access and send a notification to the administrator).
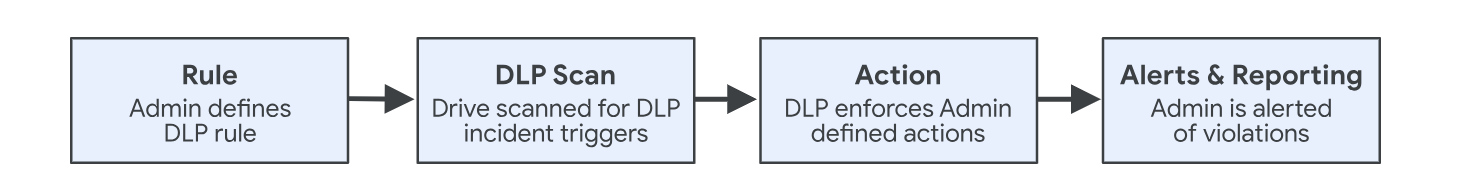
The DLP tool continuously scans Drive (both individual user drives and shared spaces) for violations of previously defined rules.
If the tool detects unwanted events, it takes Actions according to what was specified in the DLP rule: either sends an alert or blocks the action.
By combining DLP rules with optical character recognition (OCR), the specified sequence of events will be executed even if the assistant tries to send a photo of the credit card. OCR will scan the image file and recognise the character string as the card number. Find out more about Data Loss Prevention and how to protect sensitive data.
3. Security Center
This is a space in the Google Workspace admin console that has been divided into three smaller sections: a dashboard with security reports, a threat analysis tool, and a feature to help determine whether the instance’s security level is sufficient.
Dashboard
The Dashboard displays advanced security reports. Admins can specify the domain and date range they want to analyse. The reports cover events such as:
- Sharing files outside the domain
- Receiving suspicious attachments
- Suspicious activities on devices
- Failed login attempts
- Information about the number of messages that were authenticated and encrypted at a given time
- Incidents of DLP rule violations.
If any event seems suspicious, the admin can investigate the matter. For example, the report allows them to view the contents of sent and received messages and check what was in the document that the user shared outside the organisation. If that’s not enough, they can use the threat analysis tool.
Threat analysis tool
This section is designed to identify security and privacy issues within the domain. You can analyse information about specific devices or users here. Administrators also have access to information from application logs (e.g., Drive, Gmail, Calendar, or Meet), as well as logs from administrators, data studios, and the password vault.
Security level
Of course, prevention is better than cure, so it’s worth securing your instance in a way that prevents users from taking actions that could potentially harm the company. But how do you know if the console is configured correctly? The Security level tab helps with this, allowing you to verify which elements are set up securely and which still need improvement.
In the case of insufficient security measures, the application suggests to the administrator what should be done to better configure the service. For example, in the Calendar Access Settings, the following recommendation may appear: “Limit sharing of calendars outside the organisation to show only Free/Busy information. This reduces the risk of data leakage.”
4. Google Vault
Finally, let’s take a look at a tool available in Google Workspace in both the Enterprise and Business Plus packages: Google Vault, an application for storing, blocking, searching, and exporting user data.
With this tool, you can manage information such as:
- Gmail messages
- Files on Drive
- Google Chat messages (with history enabled)
- Google Meet recordings and related chat history, surveys, and question and answer session logs
- Google Group discussion messages
- SMS messages, voicemails, their transcriptions, and Google Voice call logs for Google Workspace
- Google Sites (new version)
- Messages from the classic version of Hangouts (with history enabled)
How can you use Google Vault in your organisation? For example, by specifying how long you will keep all employee email messages. This data will remain available in the application even if the user deletes the emails from their mailbox. This tool often provides invaluable support in the event of any legal disputes.
More about Google Workspace security
While the knowledge and experience of individuals delegated to protect information are essential, even the most talented admin will be powerless if they are not equipped with the tools to do their job well. Check how much control admins have in Google Workspace.
Also, remember that processing personal data is a huge responsibility that goes beyond protecting your company’s interests. Leaks of such information most often lead to its unlawful use. If you want to know more about Google Workspace compliance with legal regulations, read more in our article.
Gartner experts estimate that by 2025, up to 99% of cloud security incidents will result from user errors. If you are not sure whether your company’s data is adequately protected, we can help you verify it. At FOTC, we offer a security audit that involves a detailed examination of your Google Workspace instance’s settings for data leak protection, cyberattacks, and dishonest employee activities. As part of this service, we thoroughly analyse over 150 risk points in eight key areas.
Read more about:
