“Trust but verify” may have once seemed like a wise access policy. But the growing number of threats both from the inside and from the outside have forced enterprises to rethink their access controls and implement stronger data loss prevention measures. That’s where Google Zero Trust policy comes into play.
Table of contents
Organisations all over the world build their infrastructures and secure them with a seemingly impenetrable wall, designed to safeguard access to company secrets. It could be password protected, it could even apply two-factor verification, but the principle stays the same: once you’re behind “the wall,” you are considered “safe.” And that’s a mistake.
When the wall crumbles
When 20 big tech companies were attacked in 2009, the industry realised that their cloud network security needed a serious overhaul. Data protection came into the spotlight. New measures, especially for sensitive data, were devised and implemented.
A Zero Trust security model came to be the industry standard. As many as 83% of global organisations are committed to migrating to zero trust security policies, according to the latest, 2022 Forrester research.
Insider problem
Several factors make the previous “castle wall defence” obsolete, including: remote work, threats from the inside (including the BYOD policy many companies have implemented when working with contractors), multiple service providers as well as the ever growing number of devices connected to a network.
The almost exponential increase of potential threats and vulnerabilities makes it necessary to rethink access control policies. It may sound extreme, but the only way to ensure our employees can work securely is to trust no one by default, and verify each user and asset, regardless of where they are. Google is one of the biggest advocates of the Zero Trust policy.
How Zero Trust cloud security works
Under Zero Trust, there is no implicit trust based on the asset’s location (within or outside the organisation). To ensure secure access policies, Google’s cloud services and its Workspace apps have implemented a model where they reevaluate the trust of each request as it is made and test whether they should grant the user and their device access.
Individual versus group
Organisation that want to protect access to their sensitive resources can no longer rely on traditional VPN. In order to implement the Zero Trust approach, Google has devised a set of tools and procedures designed to continually verify and validate each user, only providing access to Google cloud resources to authorised users if they meet specific security requirements. The system collects as much information about the state of resources and the state of infrastructure as possible to keep improving security.
Identity Aware Proxy
In order to be able vet every access request Google ensures real-time visibility into all identity attributes of both the user and applications they use and access, including:
- User identity and authentication protocol (are they really who they claim to be?);
- Credential type and privileges (which may be different from different devices);
- Behaviour patterns (to flag any suspicious activity), including AI-powered suspicious activity and attack recognition;
- Endpoint device information (to check if the user has changed their hardware and clarify any discrepancies);
- Geolocation (to verify whether the user is where they claim the are);
- Software and OS updates (to ensure the user is not vulnerable to outside attacks due to outdated software versions)
- Applications installed on user devices (to check for malware on the endpoint)
Context policies
But how do we decide when and how to grant access to corporate resources? Google Cloud experts recommend a set of comprehensive context-based policies that regulate types of users and what kind of access they should have, and not on location or access credentials.
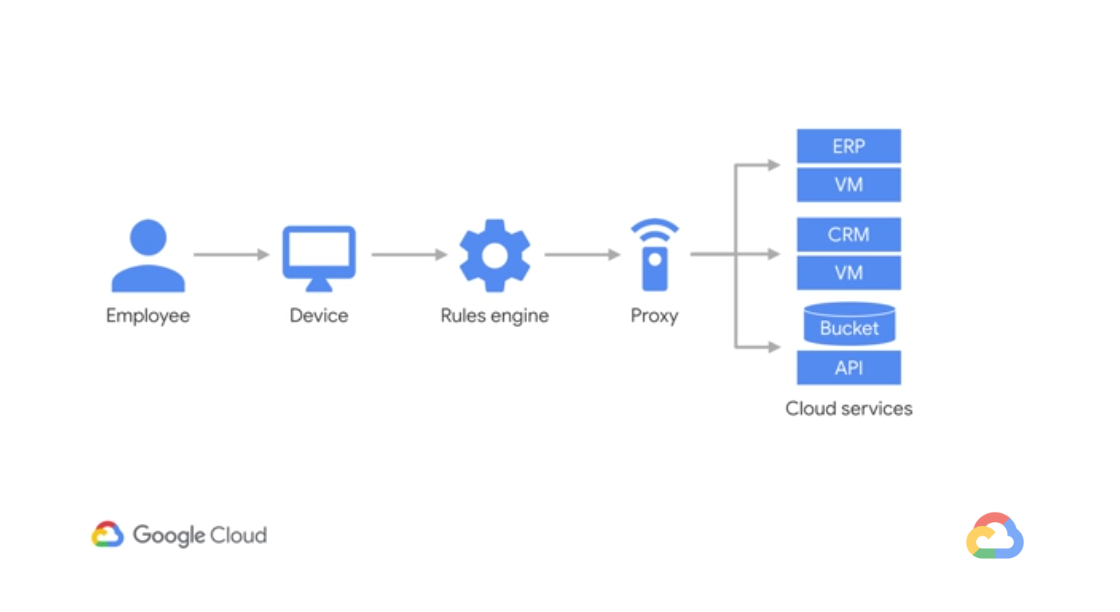
All users and individual devices are treated equally regardless of whether they have “cleared the perimeter” or not. This way an organisation is equally protected from threats on the outside and from the inside (i.e. malicious internal actors). We must distrust the assets within our infrastructure just as much as those in cloud environments. The way Google ensures that all users can securely access specific resources is through BeyondCorp.
BeyondCorp Enterprise
BeyondCorp is Google’s implementation of Zero Trust. It builds upon a decade of experience at Google, combined with ideas and best practices from the community. They way BeyondCorp works is that all decisions about granting access to specific resources are made by an access control engine. By shifting access controls from the network perimeter to individual users, BeyondCorp enables secure work from virtually any location without the need for a traditional VPN.
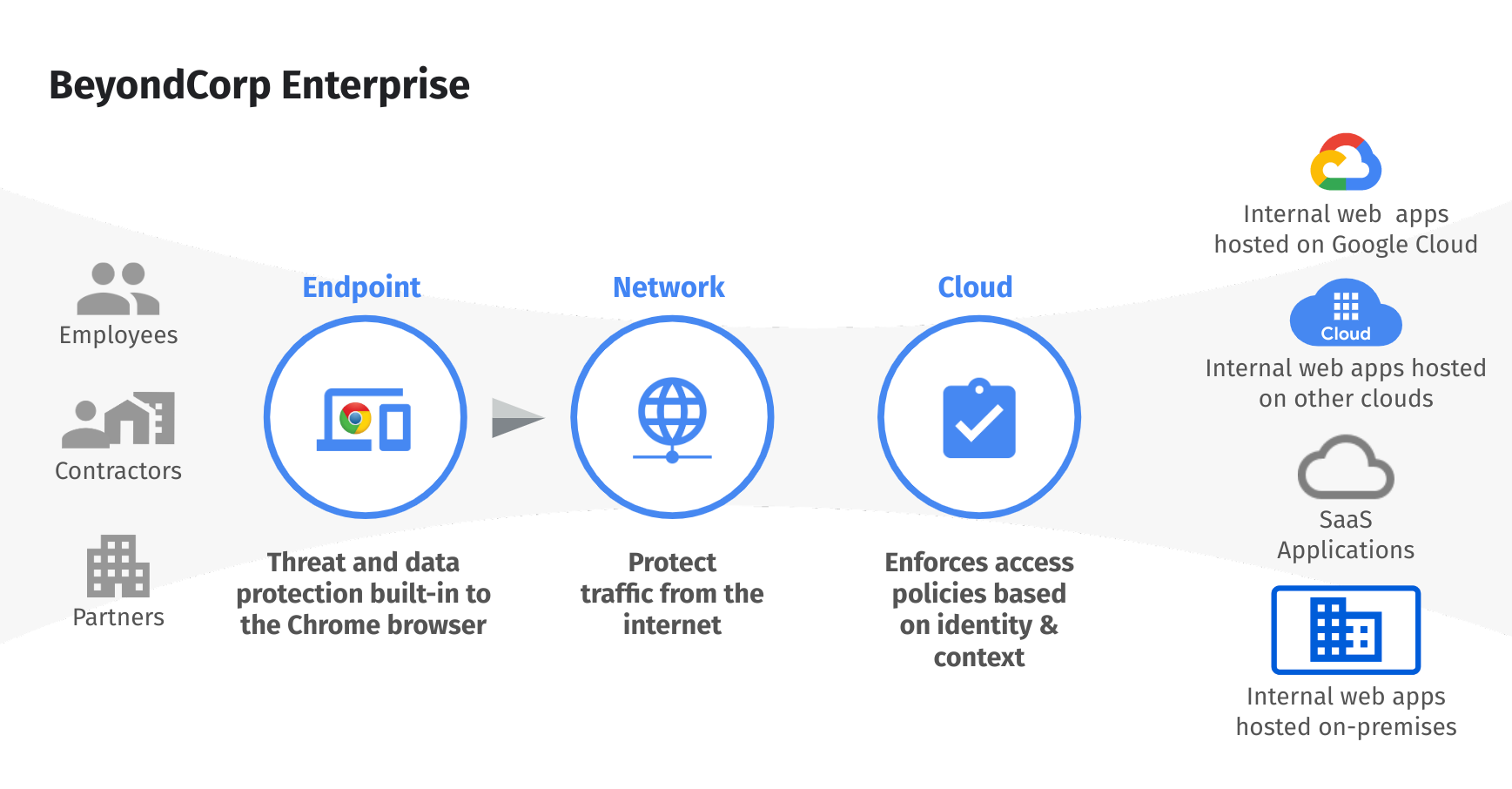
How can BeyondCorp Enterprise help my organisation?
In the Zero Trust model, there are no trusted or untrusted networks and accessing resources is subject to constant verification. Every authorisation must be based on the role of the user and the tasks they are about to perform.
The first step to improve your enterprise security is by deciding which groups of users need access to which resources and how to limit access to only those authorised. For instance, Frontline workers may only need access to point-of-sale system, while call centre workers may only require internal, browser- based call center apps. Similarly, vendors utilize BYOD and only need access to certain apps.

By implementing the Zero Trust security model in your network, you:
- Safeguard customer records and their Personally Identifiable Information (thus ensuring compliance with regional data protection policies);
- Secure corporate records and sensitive information;
- Prevent exfiltration of code and confidential information;
- Protect guest payment info and block employee web surfing.
